Mobile Threat Defense:
enhance your mobile security
Companies are widely adopting mobile devices, both smartphones and tablets, to enhance the productivity of employees and partners. Security must embrace mobile as the new perimeter to get into control. Samoby provides endpoint security silently, with full visibility of all the mobile threats, providing insight in case that a mobile forensic analysis is required, and integrates seamlessly in the already deployed UEM or mobile management solution.
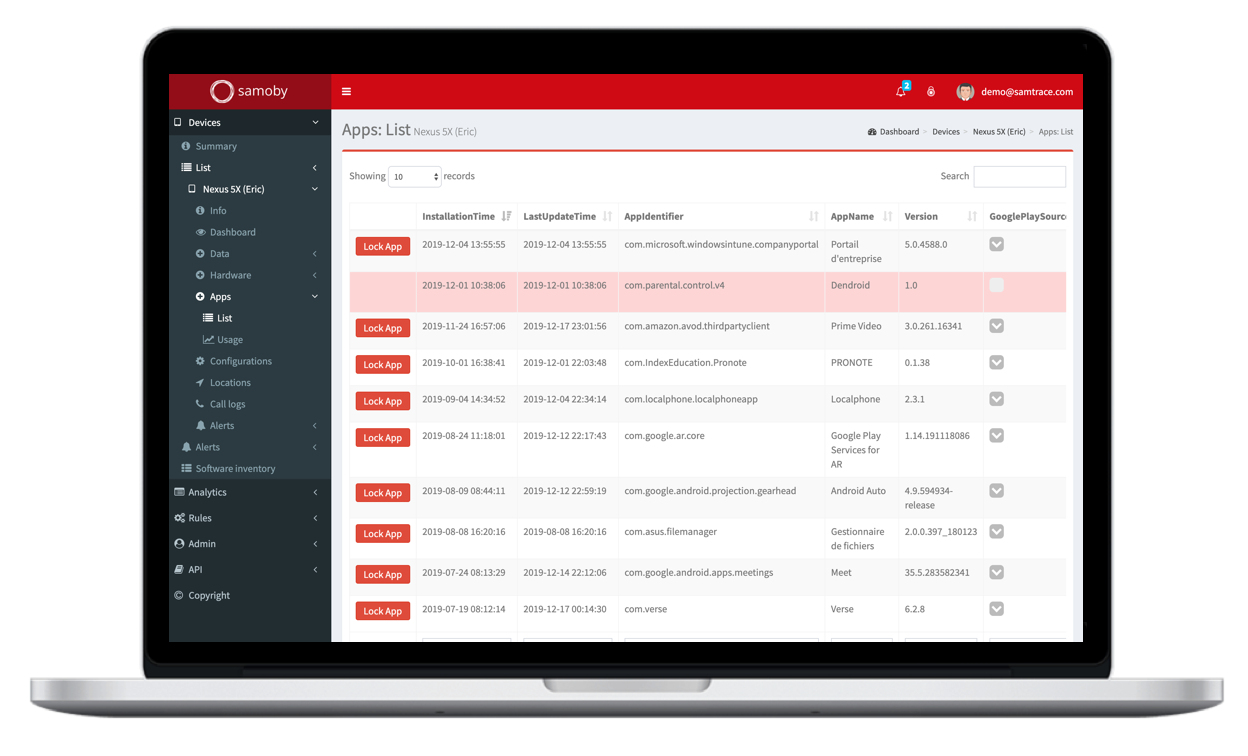
Mitigate mobile app threats
Mobile malware is widely spread in malicious apps available even in the official app stores. Sensitive data is managed through mobile devices, increasing the risk of exposure. Samoby can prevent from exfiltration of data.
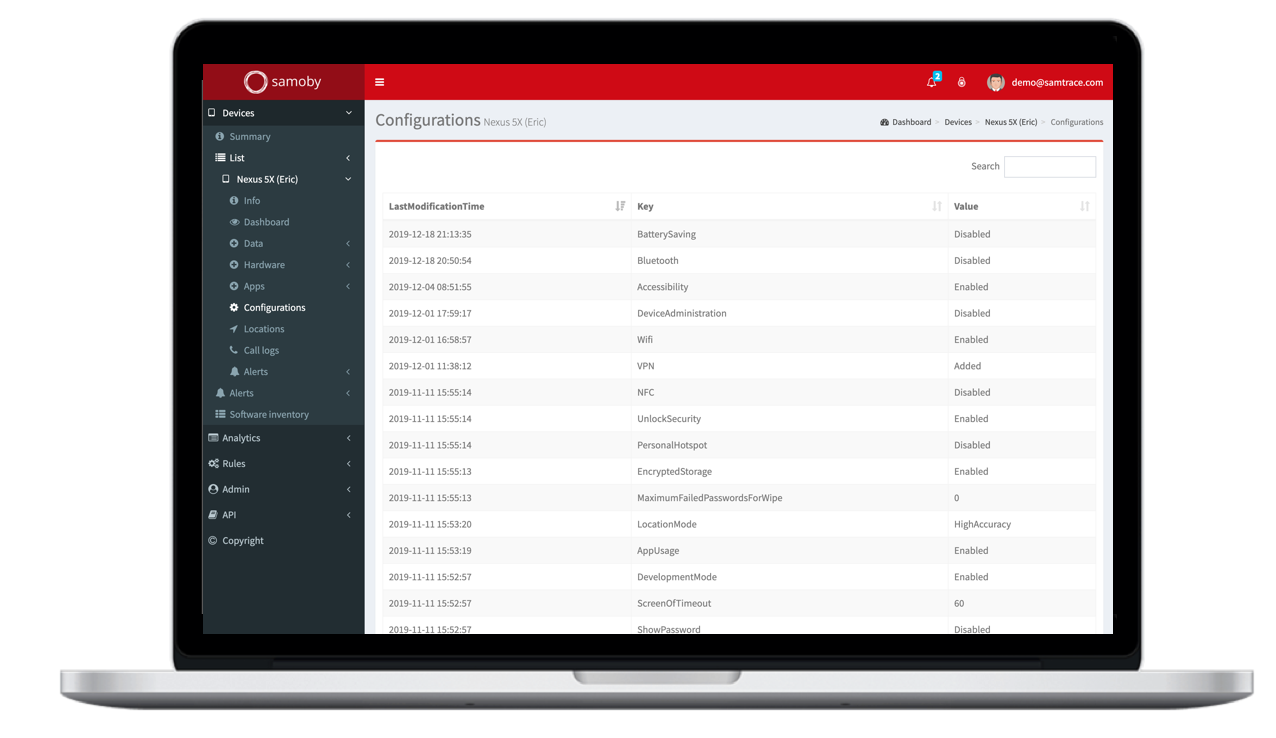
Manage device-based threats
Device configuration is key to ensure user protection: which OS version are you running, is your OS the stock version of the manufacturer or has it been corrupted, has your device been rooted or jailbreaked, have the userset up basic security measure such as encryption or access password?
Samoby detects and prevents from threats like:
- Root or jailbreak
- Non updated OS
- Suspicious behavior of the device
- Misconfiguration of the device
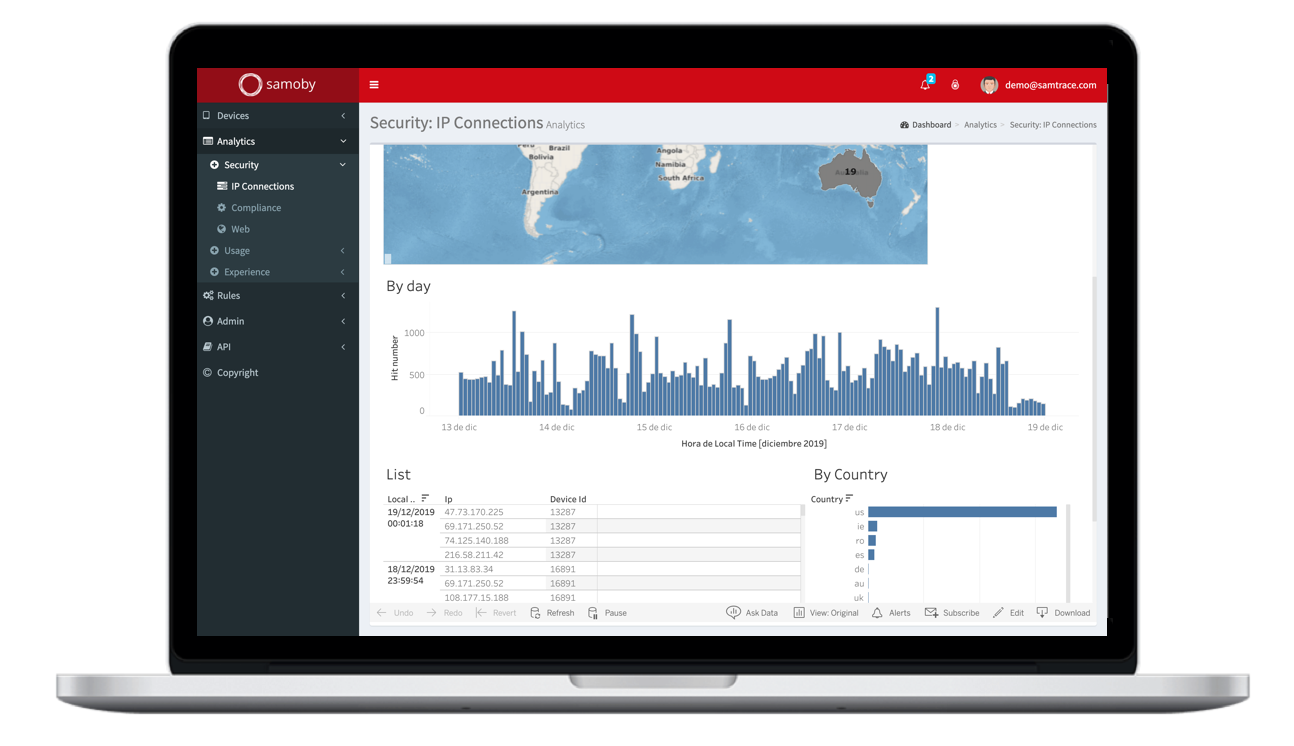
Detect and avoid network-based threats
What attackers want is to get access to your confidential data, and the most confidential is the one you send through the network: users and passwords, banking details, emails, etc.
To do that, they might try to intercept your communications using Man in the Middle Attacks (MiTM), in order to have you send your information to them instead of your usual providers.
Samoby acts directly on the endpoint, with no need to derivate traffic to third party servers, providing more privacy and reliability that its competitors. Samoby detects all kind of network attacks , like:
- MITM or Man-in-the-middle
- 3/4G to 2G downgrades
- Host certificate hijacking
- SSLStrip attacks
- TLS protocol downgrade
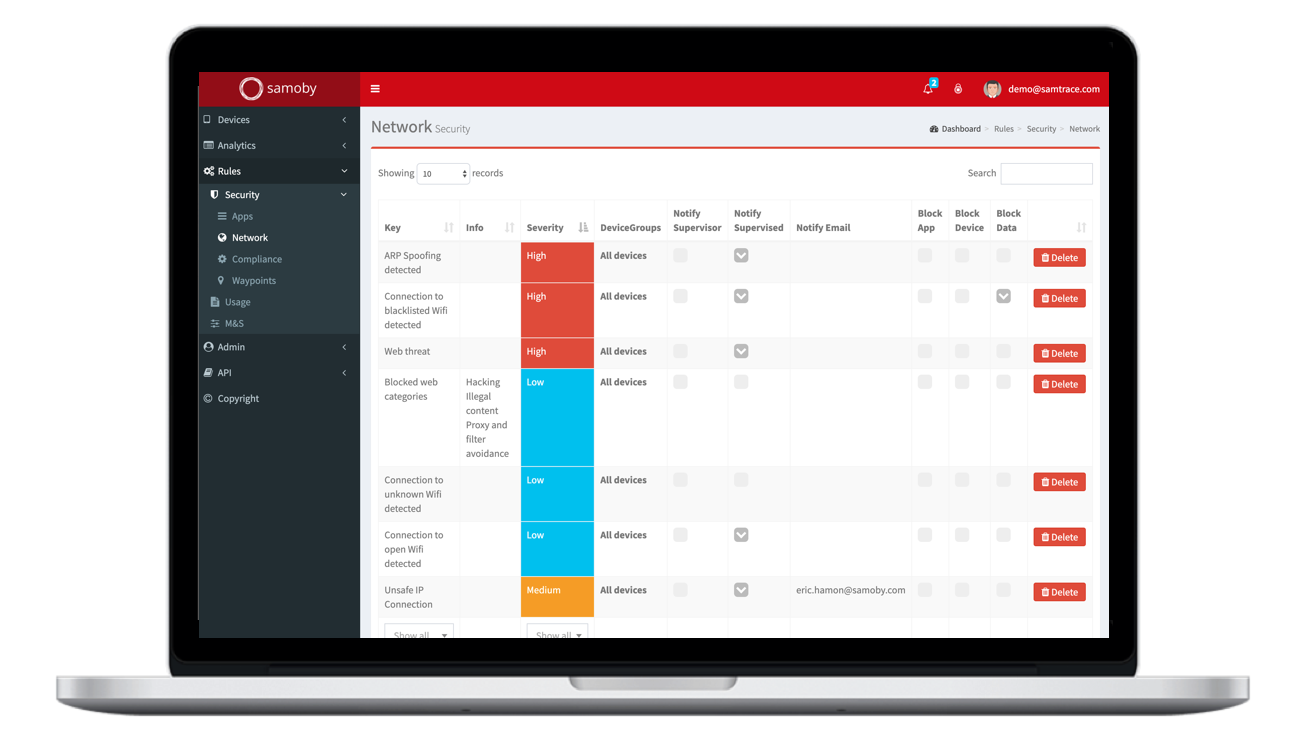
Avoid access to sensitive data when compromised
Samoby monitorizes continuously the security of the mobile endpoint and can deny access to corporate data and servers, covering both company owned devices and unmanaged ones.
With Samoby the corporate access can be blocked instantly when the OS apps, network, and device are not compliant with security policies.
Samoby benefits
Detect insider threats
Detect unusual behaviors, such as large data transfers, unknown or suspicious destinations, or downloading confidential files.
Real Time Reporting and Analytics
Monitor mobile security and usage events for smartphones and tablets in real-time, by individual, department, job role, or project.
Forensic
All historical data is stored on cloud servers, available for subsequent analysis for forensic purposes, behavioral analytics, or to determine the impact of an attack on other devices. Additionally, all the data we gather can be imported using our restful API by any tools for further analysis or consolidation with other data sources, for example in existing SIEM software.
Compliance and mitigation
Rules can be defined to automatically react when a potential threat is detected. All devices can be verified for defined threshold requirements for use, such as: OS authenticity, minimum OS version & patches, storage encryption, disabled debug or developer mode settings, and app wrapping.
Alerts and Monitoring
Automatic alerts and remediation tasks can be configured to respond to security threats. Quickly visualize and analyze information to identify problem areas and potential security threats. The platform provides constant monitoring to generate informative, customizable real-time reports.
Self-Service
Detect and inform users about service outages or quota limits to help them solve problems autonomously.
Talk to Samoby sales team and have a walk through our products


